Microsoft 365 Copilot: Revolutionizing Work With AI
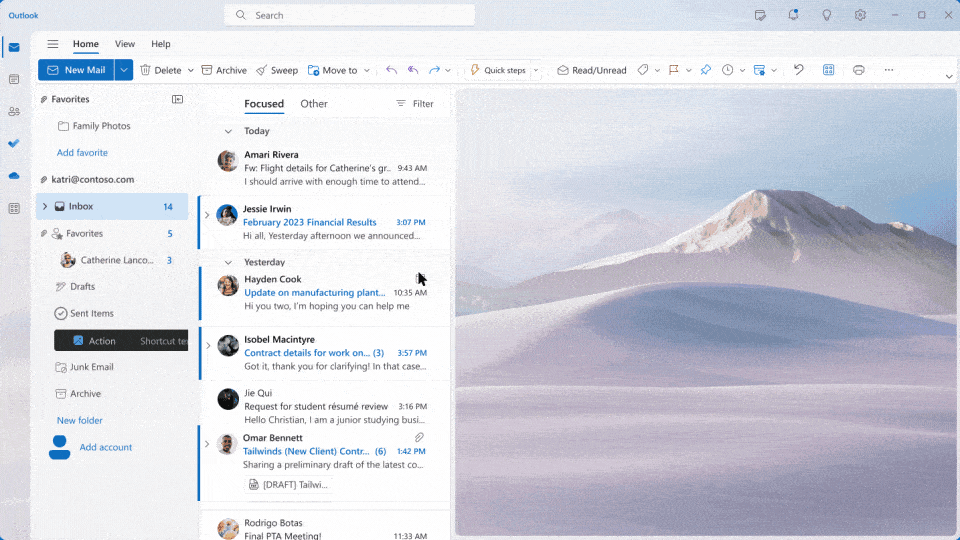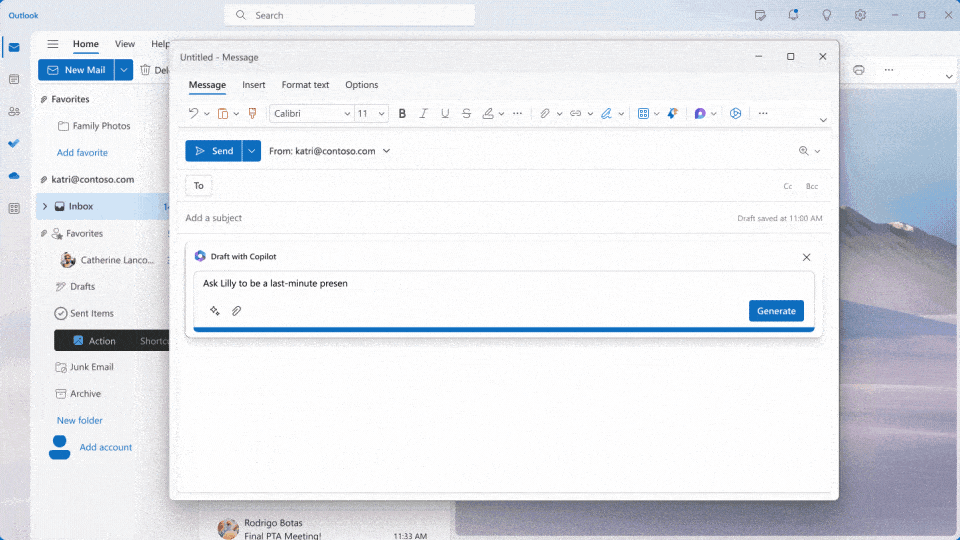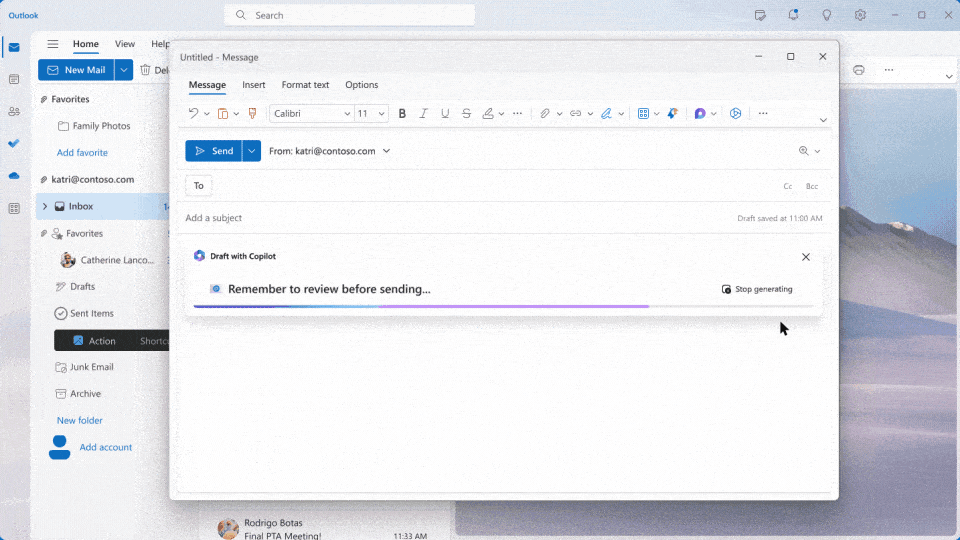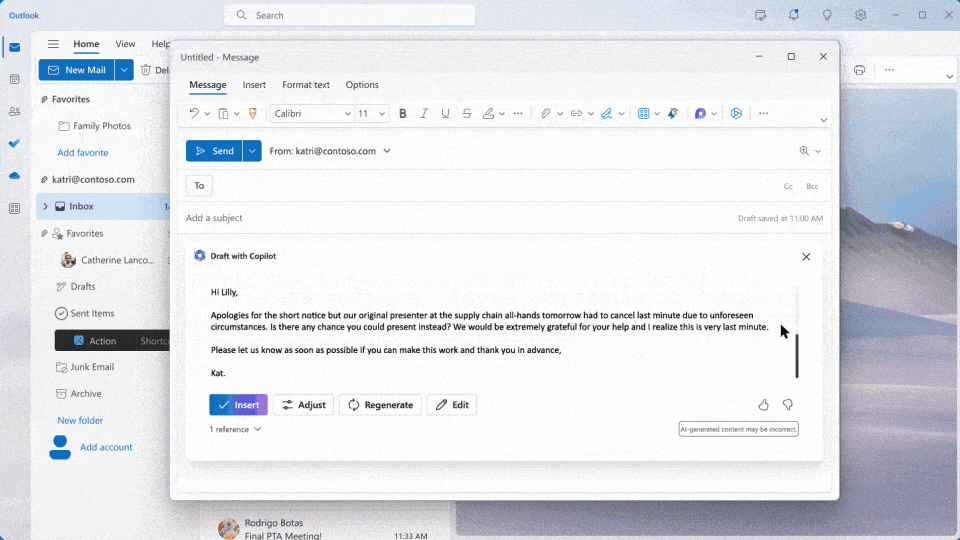
Microsoft is transforming work with Microsoft 365 Copilot, an AI-powered assistant that integrates with popular apps like Word, Outlook, and Teams. Leveraging advanced natural language models and deep learning, Copilot acts as your personal Copilot, understanding your needs and streamlining workflows. Copilot boosts productivity and creativity for enterprise customers by automating repetitive tasks, taking meeting […]
How Popular Culture Influenced Our Technology

You may think that popular culture has no real impact on our technology, but you would be mistaken. Popular culture has played a significant role in shaping the technology we use today. From science fiction books and movies that inspired groundbreaking inventions to music that influenced technological trends and even gaming that pushed the boundaries […]
Tip of the Week: Improve Your Privacy When Using LinkedIn

LinkedIn is a fantastic social platform for workers around the world, but as with any type of social media, you need to be aware of your data privacy when using this site. Today’s tip of the week will help you discover how to improve your privacy when using LinkedIn in the future. When you adjust […]
Tip of the Week: Scan Picture or Document to PDF in Android

Many people don’t realize that their mobile device can double up and offer them many of the same great features that a PC or laptop could. A hidden secret that very few people take advantage of is the fact that Google Drive offers you the chance to scan a document or picture and create a […]
Tip of the Week: Disable Wi-Fi Calling on Your Android Device

As mentioned in the title, this article is for Android users and Wi-Fi calling. As an Android user, you probably noticed the Wi-Fi calling option you get when you make or receive a call while connected to a network. This can be a great tool to use if you ever find yourself without cell service. […]

